hacking
How Much Ram Do I Need for Pentesting?
Pentesting or ethical hacking can be an amazing career selection for individuals with strong computer and →
How to Bypass Administrator Password on Dell Laptop?
Having to forget the laptop’s password is bound to happen if you’ve been using a Dell →
Car Hacking Danger Is Likely Closer Than You Think
A Detroit Free Press report shows there were 150 automotive cybersecurity incidents in 2019 alone. It →
PKI Solutions: 5 Reasons Why Businesses Should Consider them
We are living in a digital world, but most of us are totally unaware of how →
Razer BlackWidow V3 Mini Review
Introduction The Razer BlackWidow V3 Mini is 65% the size of a standard gaming keyboard, with →
Watch Dogs: Legion – Bloodline (for PC) Review
Watch Dogs: Legion, the third installment in the Watch Dogs series, lacked focus. The “play as →
EA hacked: Battlefield 2042 maker hit by huge data breach
Gaming giant Electronic Arts (EA) has been hit by a major data breach that has allegedly →
Watch Dogs Legion finally gets its online mode next month, and it’s completely free
Several months after the base game’s original release, Ubisoft has announced that Watch Dogs Legion’s multiplayer will →
MacOS users targeted with dangerous new malware
Cyber threats are increasingly targeting macOS users and new research from Trend Micro has discovered that →
Watch Dogs: Legion — Gameplay, trailers, release date, and everything you need to know
Get ready to travel across the pond because Watch Dogs: Legion players are going to London. →
eCommerce Website Security: How to Protect Yourself and Your Customers
In today’s word, we have become more open to e-commerce. Nowadays, a lot of young entrepreneurs →
Crownline 320 LS Boat Review
Overview: The Crownline 320LS is ideal for daytripping or a comfortable overnight stay. Main Features: Simple →
Hands on: Watch Dogs Legion Preview
Watch Dogs Legion is the third entry in Ubisoft’s open-world hacking franchise, this time taking players →
Major Thunderbolt security flaw found in Macs and PCs: Should you be worried?
A series of vulnerabilities in Thunderbolt 2 and 3, collectively called ‘Tunderspy,’ can leave your Mac →
The National Cyber Security Centre has issued safety advice for security cam users
The National Cyber Security Centre (NCSC) has created a safety checklist for anyone still brave enough →
Human error to blame for errant ‘Mercedes me’ alerts
Users of Mercedes’ popular smartphone app were sent random, oddly-worded messages last week Mercedes-Benz has confirmed →
Tesla Model 3 vulnerability exposed at Pwn2Own; hackers take home the car
A pair of security researchers who revealed a security issue for the Tesla Model 3 at →
2018 Triumph Tiger 1200 XCa Review
Speaking of adventuring, on my way home from flogging this new Tiger all over the mountainside, I was →
Raspberry Pi: Everything you need to know
How to get started with this $35 mini-PC that’s beloved by makers and DIY enthusiasts. The →
Suzuki DR-Z400SM First Ride Review
The list of factory-equipped supermoto motorcycles in the US is short, real short. Really, one model →
Huge 1.3m Dodge Ram recall as FCA woes continue
Fiat Chrysler Automobiles (FCA) has been dealt yet another blow in the form of vehicle recalls. →
Volkswagen has spent two years trying to hide a big security flaw
Thousands of cars from a host of manufacturers have spent years at risk of electronic car-hacking, according to expert →
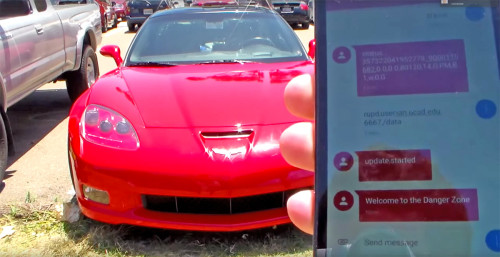
It’s the Chevy Corvette’s turn to get hacked
Car hacking seems to be the new black recently. As cars get smarter, they also become →
Tesla Courts Hackers to Defend High-Tech Cars
Hackers swarmed a Tesla sedan in a ‘hacking village’ at the infamous Def Con conference on →
Tesla hacked: car can be shut down via connected laptop
As the auto industry and security community is still reacting to the new about a Jeep Cherokee →
Silent Circle tries again: Blackphone 2 for Android for Work
Given all the news about spying and hacking, you’d think mobile users would be more conscientious →
Critical Internet Explorer 11 security vulnerability
Researchers from the security company Vectra have discovered a high-severity vulnerability in Internet Explorer 11 which →
Hacking Team helped Italian police to hijack internet addresses
The Border Gateway Protocol (BGP) is used to route traffic across the Internet — and it’s →
Hacking Team hack casts spotlight on murky world of state surveillance
In contrast to many of the private companies performing outsourced aggressive surveillance work for the world’s →
Breach at Italian Surveillance Vendor Prompts Security Alert
Software maker Adobe says it is fixing a critical flaw revealed by the spectacular attack on →